Category: Blog
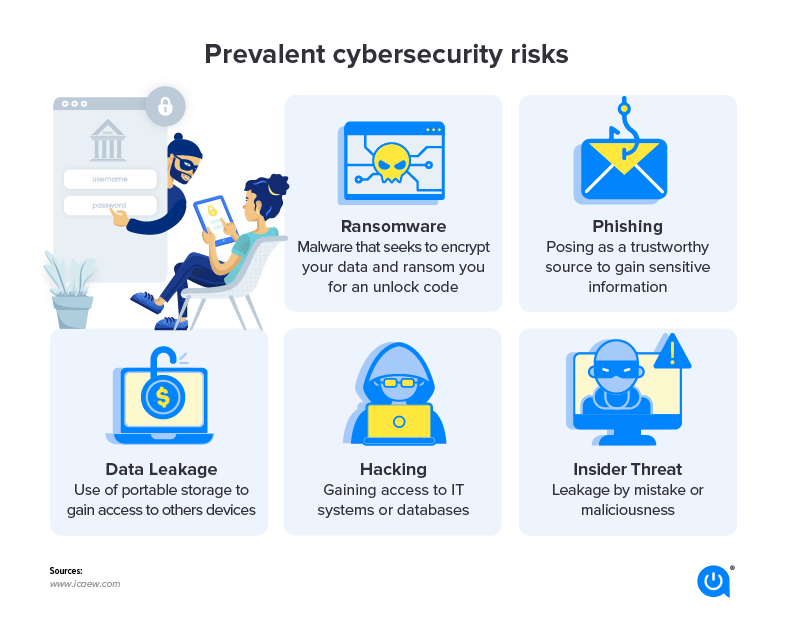
Understanding Phishing: How to Stay Safe Online
- 0
Phishing is a type of cyber attack where a fraudulent individual impersonates a legitimate institution or service to deceive individuals into providing sensitive information such as passwords, credit card numbers, and social security numbers. These attacks can occur through email, text messages, or even phone calls, and can result in financial loss, identity theft, and…
Read More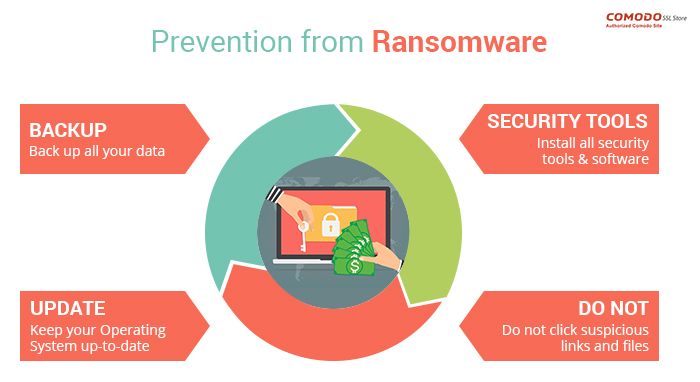
How to Protect Your Data from Ransomware Attacks
- 0
Ransomware attacks have become increasingly prevalent in recent years, with cybercriminals targeting individuals and businesses alike. These attacks involve the encryption of a victim’s data, followed by a demand for payment in exchange for the decryption key. To protect yourself and your data from ransomware attacks, it is essential to take proactive measures to secure…
Read More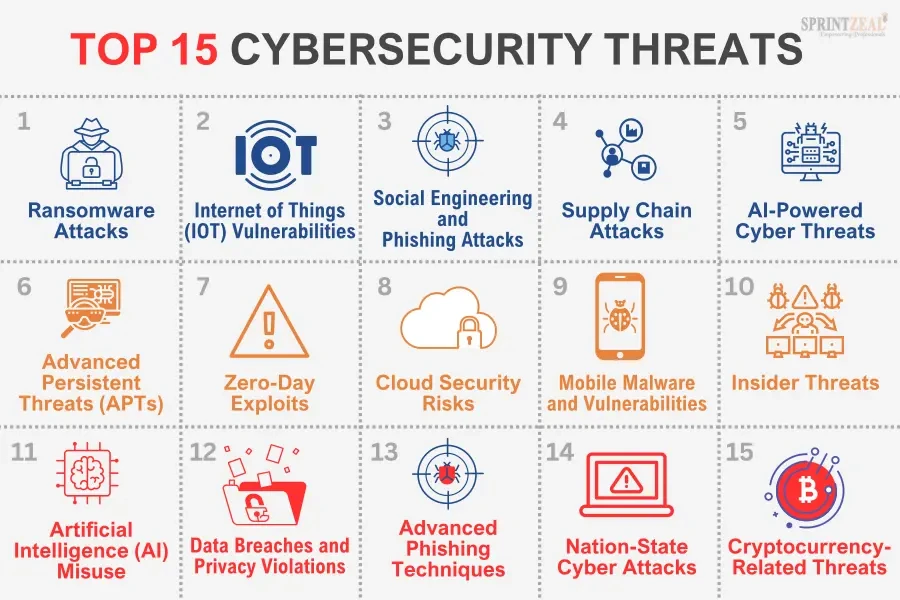
The Latest Cybersecurity Threats in 2024
- 0
In today’s rapidly evolving digital landscape, cybersecurity threats continue to pose a significant risk to businesses and individuals alike. As we look towards 2024, it is crucial to stay informed about the latest trends in cyber threats to ensure the security of our data and systems.
Read More
Essential Cybersecurity Practices for Small Businesses
- 0
In today’s digital age, cybersecurity is more important than ever for small businesses. Without proper protection, businesses are vulnerable to data breaches, malware attacks, and other cyber threats that can have devastating consequences. Implementing essential cybersecurity practices is crucial for safeguarding sensitive information and maintaining the trust of customers.
Read More
Common Mistakes to Avoid in Software Testing
- 0
Software testing is a critical part of the software development process, as it helps ensure that the final product is free of bugs and meets the expectations of its users. However, there are some common mistakes that many software testers make that can compromise the quality of the testing process and ultimately the quality of…
Read More